by Paul Siegel

A common theme of this blog is offering large scale solutions on a budget. In these tough times many organizations are evaluating Google Apps as cost effective replacement to in house e-mail solutions. For organizations running Active Directory many are turning to Google's recently released Google Active Directory Sync tool or NetIQ's Gmail Connector for NetIQ Identity Manager(formally Novell IDM) for safely moving users passwords from their domain to the cloud. Some smaller organizations don't have the luxury of these higher directory solutions either due to cost or environmental factors, which is what makes Google Apps appealing in the first place. There is another opensource solution that often seems overlooked. Google Apps Directory Sync Tool supports OpenLDAP with password sync without making the userpassword a plain text attribute. This configuration uses only one tool for creating , deleting , suspending , and password synchronization from your openLDAP directory to your Google Apps Domain.
Google offers excellent documentation of Google Apps Directory Sync Tool located here:
http://commondatastorage.googleapis.com/enterprisetraining/gapps/admin/DirSync_GoogleApps/en/DirSync_GoogleApps.html
http://commondatastorage.googleapis.com/enterprisetraining/gapps/admin/DirSync_GoogleApps/en/DirSync_GoogleApps.html
Should one decide to investigate this route there are some basic openLDAP configurations to be aware before attempting to sync users.
1. Create a Password Policy
Default configuration of openLDAP will not have a password policy. User objects created will have a clear text password unless specified during creation. For this scenario we will need passwords to be hashed by default.
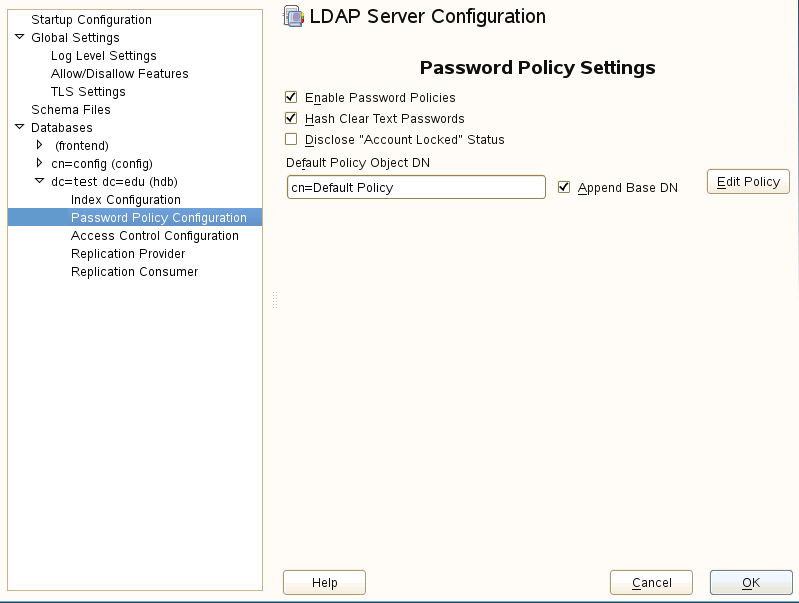
Open your ldap server configuration utility. Accessing this utility varies per Linux distribution In Opensuse open yast then Ldap Server. Expand out the database arrow on the left, then expand all options beneath it. You will see your domain listed. In the example pictured below it will be dc=test,dc=edu. Highlight Password Policy Configuration to bring the menu forward and check "Enable Password Policies" and "Hash Clear Text Passwords"
Open your ldap server configuration utility. Accessing this utility varies per Linux distribution In Opensuse open yast then Ldap Server. Expand out the database arrow on the left, then expand all options beneath it. You will see your domain listed. In the example pictured below it will be dc=test,dc=edu. Highlight Password Policy Configuration to bring the menu forward and check "Enable Password Policies" and "Hash Clear Text Passwords"
This will ensure that all passwords in the database are hashed at all times. The default hash in openLDAP 2.4 is salted sha (SSHA).
2. Accessing cn=config in OpenLDAP 2.4
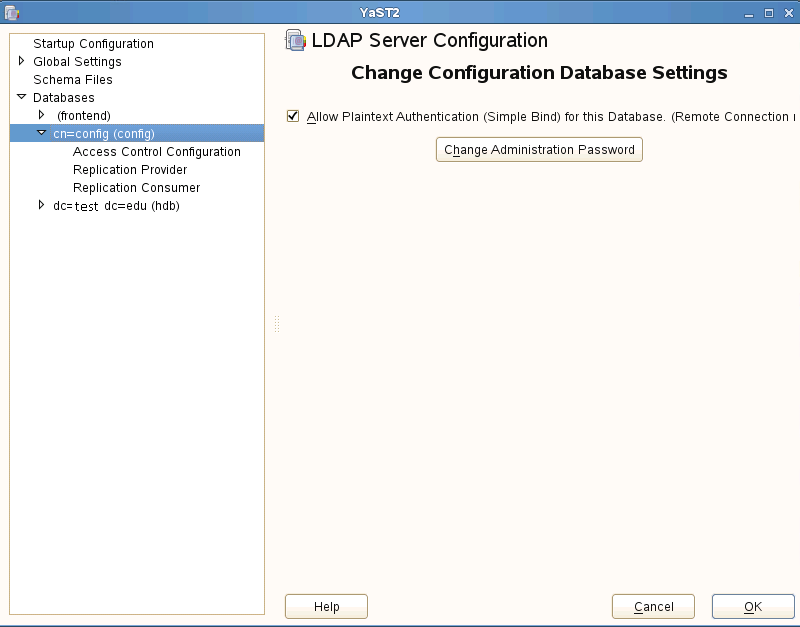
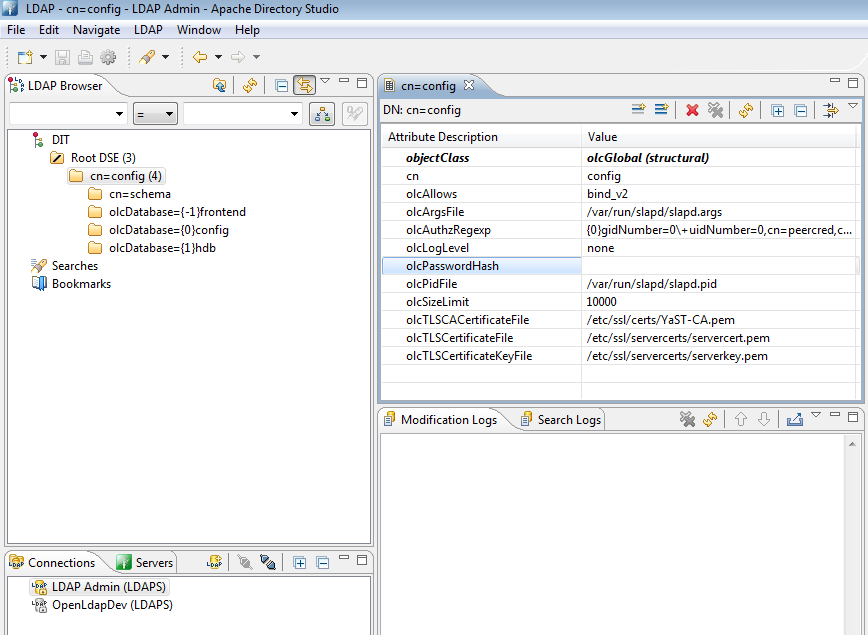
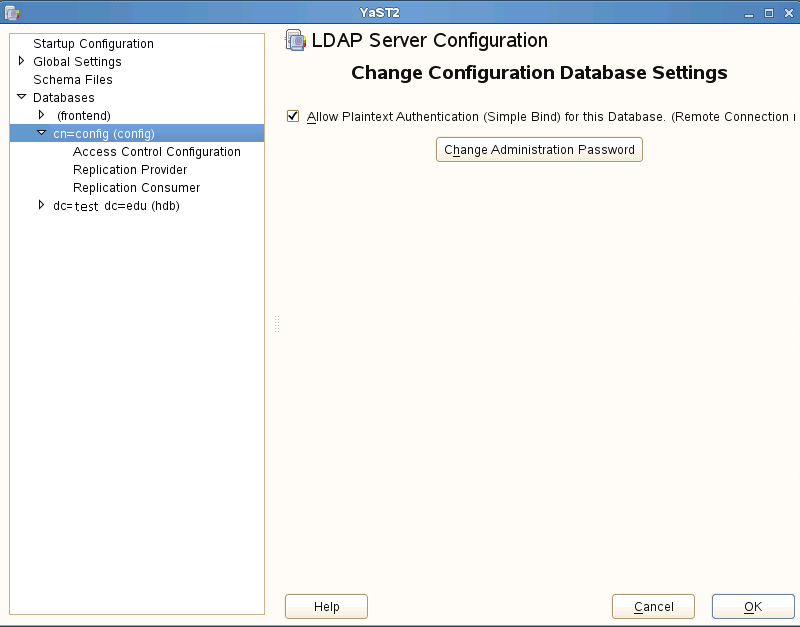
While our password policy ensures all passwords are hashed by default, openLDAP uses a Google Apps unsupported hash. The resolution to this problem is to force a new default. This is done through editing the cn=config. The cn=config is the replacement to the former slapd.conf in previous versions of openLDAP. It is a file ldif database that allows configuration of the directory without having to restart the service. The cn=config is most easily edited with a ldap browser. To configure, you must do an ssl bind to the directory using cn=config as the Bind DN and the Base DN. Before this can be accomplished, Simple Bind to the cn=config database must be temporarily turned on to allow editing. This is done through the Ldap Server utility the same way as the password policy. Under databases there will be a section for cn=config with enable Simple Bind as it's only option.
While it seems concerning to allow plaintext authentication, this connection can only be established remotely over ssl and is only turned on temporary when editing the cn=config.
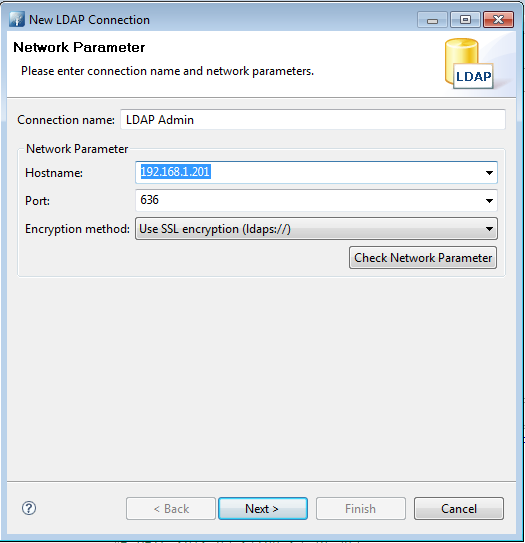
Next we have to configure our ldap browser connection. I personally prefer Apache Directory Studio for it's ease of use and ability to easily fetch operational attributes of objects. In your ldap browser add a new connection.
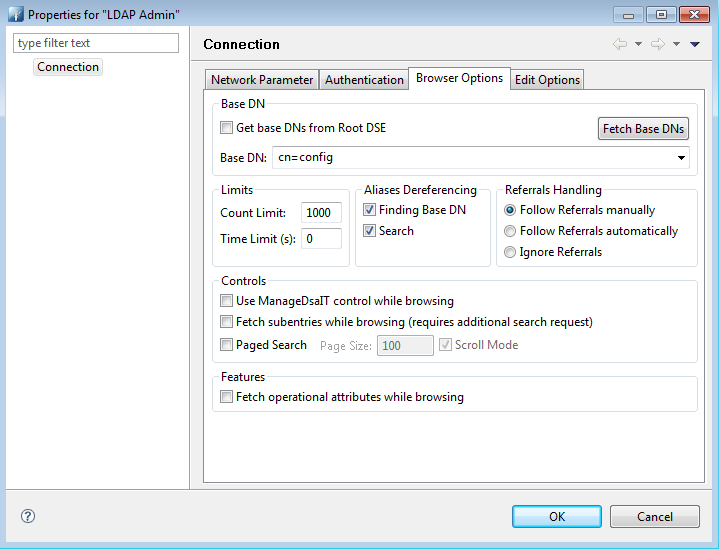
This configuration can only be done over ssl default port 636.
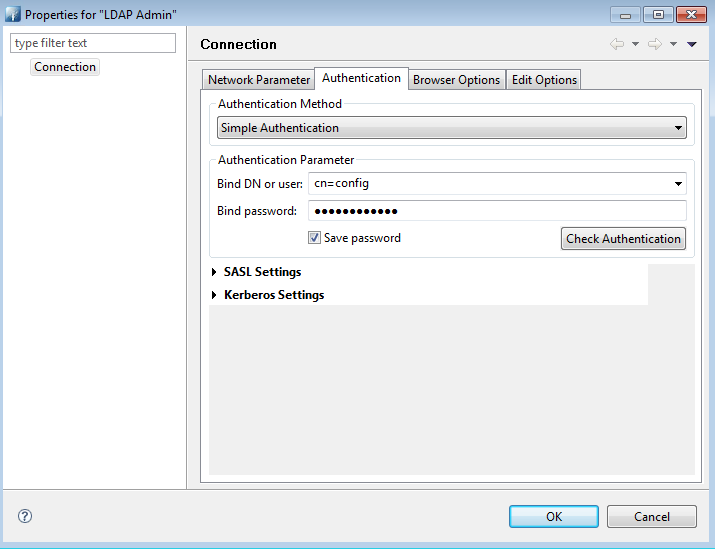
Select Simple Authentication and set Bind DN to cn=config. Apache Directory Studio offers a Check Authentication button to test settings before moving forward.
Uncheck Get base DNs from Root DSE and specify cn=config as the Base DN.
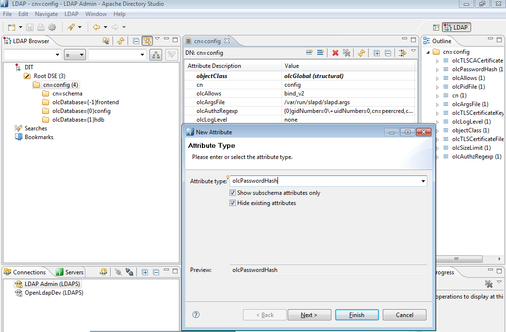
The connection end result will look like this with only the config object available as you're bound directly to it. Expand out cn=config in the LDAP Browser window and then right click and select New Attribute in the white space of the editor window.
3. Setting The Default Password Hash
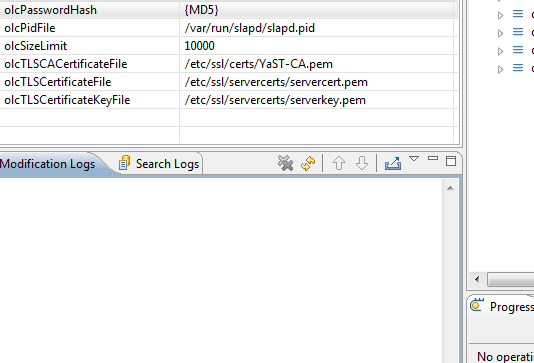
From the Attribute Type drop down menu select olcPasswordHash and click Finish.
Click in the value cell of the editor to add a value to the attribute. Google Apps Directory Sync Supports {SHA},{MD5}. For this example I'll use {MD5}.
4. Sync Away!
Go back into your ldap server utility one last time and turn off Simple Bind.
Your OpenLDAP directory is now configured to hash all user passwords to MD5. This will allow your Google Apps Directory Sync Tool to retrieve encrypted passwords from your ldap directory over ldap ssl. Google Apps Directory Sync Tool is available for Windows, Linux and Solaris, with configurable run options giving you the ability to run this tool as a cron job. This particular Google Apps deployment can be a one-server solution. Consider evaluating this solution. you may be surprised!
 RSS Feed
RSS Feed
