
http://commondatastorage.googleapis.com/enterprisetraining/gapps/admin/DirSync_GoogleApps/en/DirSync_GoogleApps.html
1. Create a Password Policy
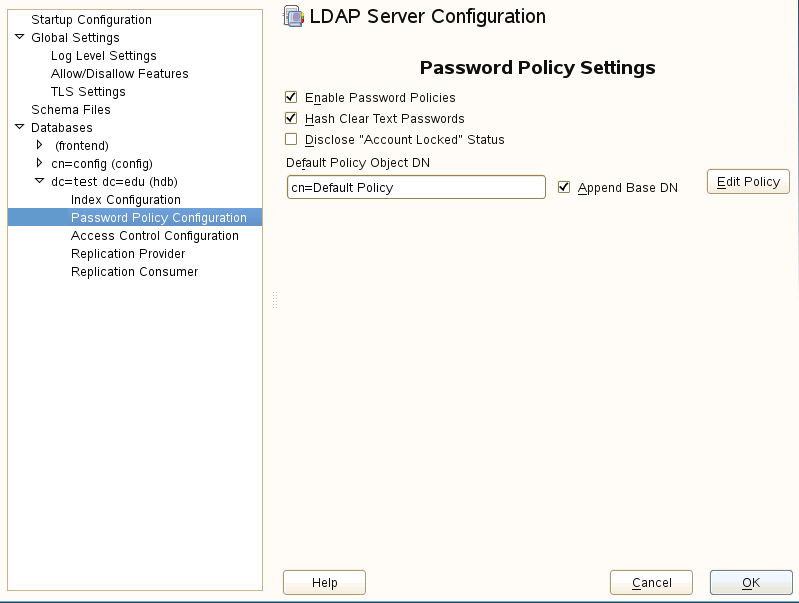
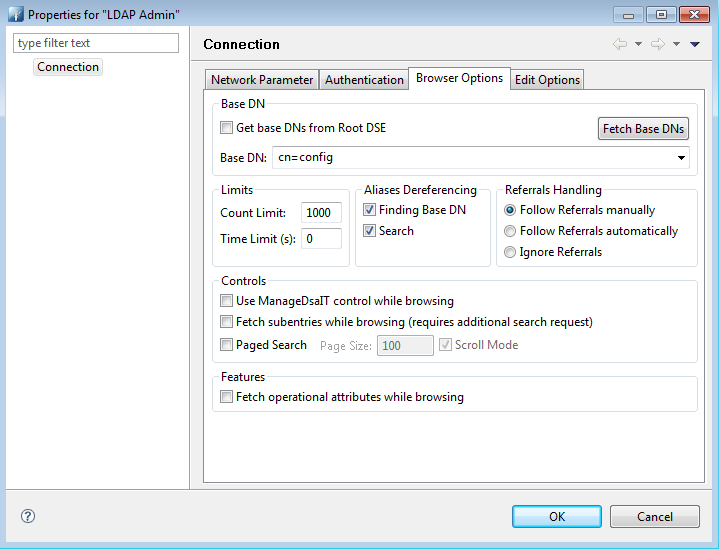
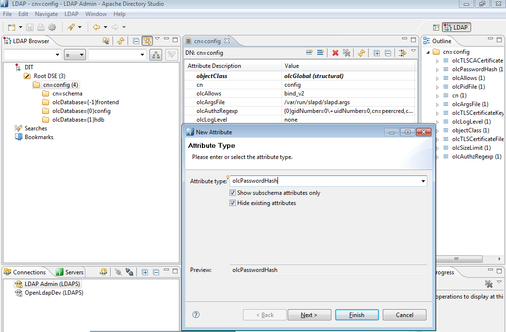
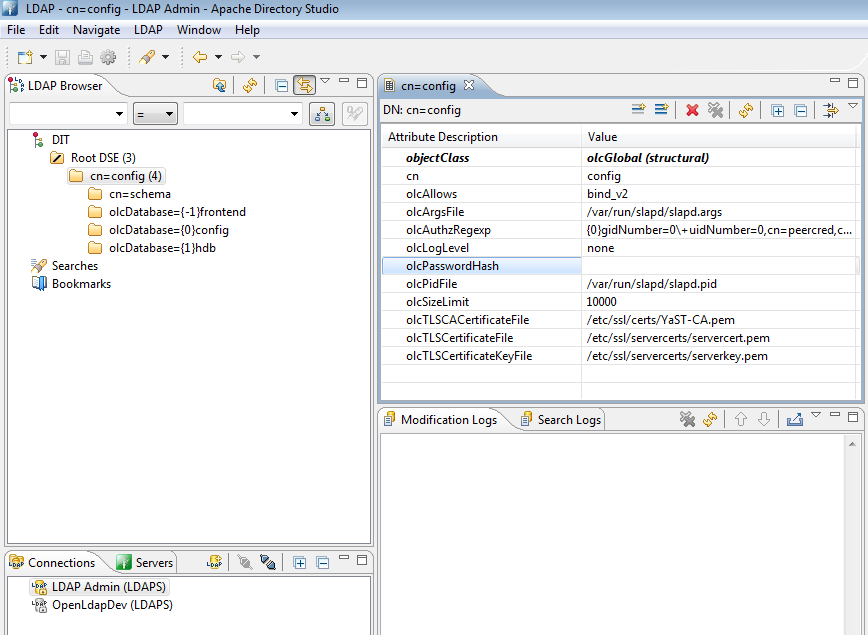
Open your ldap server configuration utility. Accessing this utility varies per Linux distribution In Opensuse open yast then Ldap Server. Expand out the database arrow on the left, then expand all options beneath it. You will see your domain listed. In the example pictured below it will be dc=test,dc=edu. Highlight Password Policy Configuration to bring the menu forward and check "Enable Password Policies" and "Hash Clear Text Passwords"
 RSS Feed
RSS Feed
